40 antivirus bypass techniques pdf
Antivirus evasion tools [updated 2021] - Infosec Resources Encrypting the binary is one of the common ways to bypass antivirus detection. The logic behind using encrypters is to obfuscate the binary from antivirus tools by encrypting it. This will be decrypted back when the binary is run. Kali Linux has got an open source encrypter named Hyperion available in it. Encapsulating Antivirus (AV) Evasion Techniques in Metasploit ... - Rapid7 Today, malicious behavior identification techniques are multilayered and include heuristics, behavioral, and cloud-based detections, in addition to static scanning. Higher complexity makes exploitation more difficult for attackers, but it can also translate to complacency among end users.
Anti-forensic techniques deployed by custom developed malware in ... The experiment [7] uses a combination of msfvenom and Veil-Evasion anti-virus framework to construct the payload able to bypass antivirus control. A significant advantage of using these tools is that they can change an existing executable file into the obfuscated executable. Such an obfuscated executable is more likely to bypass antivirus ...

Antivirus bypass techniques pdf
Antivirus Evasion | Bypass Techniques. | by Dhanishtha Awasthi - Medium 5 min read Antivirus Evasion | Bypass Techniques. While playing around with machines I came up with a very interesting scenario, where my executable payloads on as soon as getting copied to... Fileless attacks: How attackers evade traditional AV and how to stop them Navigate to Configure > Policies. Click " New " or select an existing policy. Choose the " Endpoint Detection and Response " tab. Locate " Suspicious Activity Monitoring " and enable it for the desired operating systems. Suspicious Activity monitoring detections in Nebula showing a possible fileless attack. (PDF-Doc) Antivirus Bypass Techniques Full Download | Finance PDF Antivirus Bypass Techniques PDF Download Are you looking for read ebook online? Search for your book and save it on your Kindle device, PC, phones or tablets. Download Antivirus Bypass Techniques PDF full book. Access full book title Antivirus Bypass Techniques by Nir Yehoshua. Download full books in PDF and EPUB format.
Antivirus bypass techniques pdf. Antivirus Bypass Techniques - Google Books Antivirus Bypass Techniques: Learn Practical Techniques and Tactics to Combat, Bypass, and Evade Antivirus Software Nir Yehoshua, Uriel Kosayev Packt Publishing, Jul 16, 2021 - Computer... PDF byPass_AV/Antivirus baypass techniques.pdf at master - Github byPass_AV / Antivirus baypass techniques.pdf Go to file Go to file T; Go to line L; Copy path Copy permalink; This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Cannot retrieve contributors at this time. 20.8 MB Download. Chapter 3: Antivirus Research Approaches | Antivirus Bypass Techniques Chapter 3: Antivirus Research Approaches. Chapter 3. : Antivirus Research Approaches. In this chapter, you will learn about the Windows operating system protection rings concept, we will introduce two of our real-life bypass examples, and you will also learn the basic three vulnerabilities that can be used to bypass antivirus software. Bypassing Antivirus Detection with Encryption | Request PDF - ResearchGate Abstract. Bypassing an antivirus is a common issue among ethical hackers and penetration testers. Several techniques have been -and are being-used to bypass antivirus software; an effective and ...
Antivirus & Malware Evasion Techniques - Kaspersky Another technique through which malware bypasses antivirus scanners is by encoding the payload. Cybercriminals often use tools to do this manually and when the malware is delivered and activated, it is then decoded and does its damage. This is usually done via a small header program tacked onto the front of the encoded virus. Antivirus Bypass Techniques: Learn practical techniques and tactics to ... Develop more secure and effective antivirus solutions by leveraging antivirus bypass techniques. Key Features: Gain a clear understanding of the security landscape and research approaches to bypass antivirus software; Become well-versed with practical techniques to bypass antivirus solutions; Discover best practices to develop robust antivirus ... Antivirus Bypass Techniques: Learn practical techniques and tactics to ... "Antivirus Bypass Techniques is a great book for those who are pursuing a career in cybersecurity, be it blue or red teaming. It contains not only the necessary fundamentals and examples of the bypass techniques themselves but also definitions and technical explanations of how to use and acquire those techniques. Advanced-level experts will ... Antivirus Bypass Techniques - Google Books Antivirus Bypass Techniques: Learn practical techniques and tactics to combat, bypass, and evade antivirus software Nir Yehoshua, Uriel Kosayev Packt Publishing Ltd, Jul 16, 2021 -...
Antivirus Bypass Techniques-2021 | PDF | Malware - Scribd Techniques Learn practical techniques and tactics to combat, bypass, and evade antivirus software Nir YehoshuaUriel Kosayev BIRMINGHAM—MUMBAI Antivirus Bypass TechniquesCopyright © 2021 Packt PublishingAll rights reserved. PDF dl.packetstormsecurity.net dl.packetstormsecurity.net Antivirus Bypass Techniques [Book] - O'Reilly Online Learning Start your free trial Book description Develop more secure and effective antivirus solutions by leveraging antivirus bypass techniques Key Features Gain a clear understanding of the security landscape and research approaches to bypass antivirus software Become well-versed with practical techniques to bypass antivirus solutions Antivirus Bypass Techniques | Packt Home Security Antivirus Bypass Techniques Antivirus Bypass Techniques By Nir Yehoshua , Uriel Kosayev FREE Subscription Read for free €22.99 eBook €28.99 Print + eBook Buy €11.99 eBook + Subscription Buy What do you get with a Packt Subscription? Instant access to this title and 7,500+ eBooks & Videos
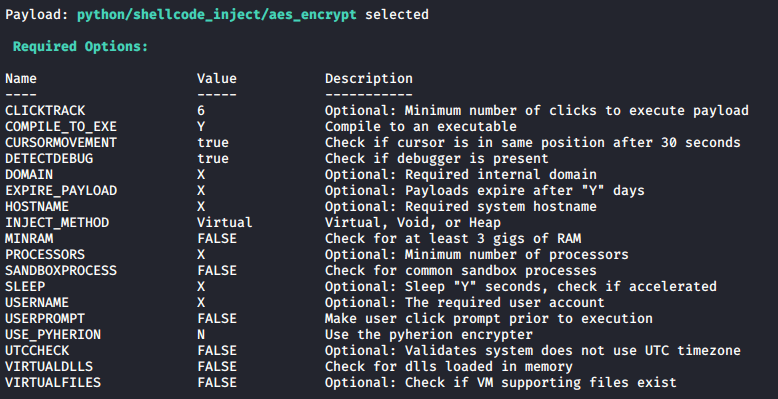
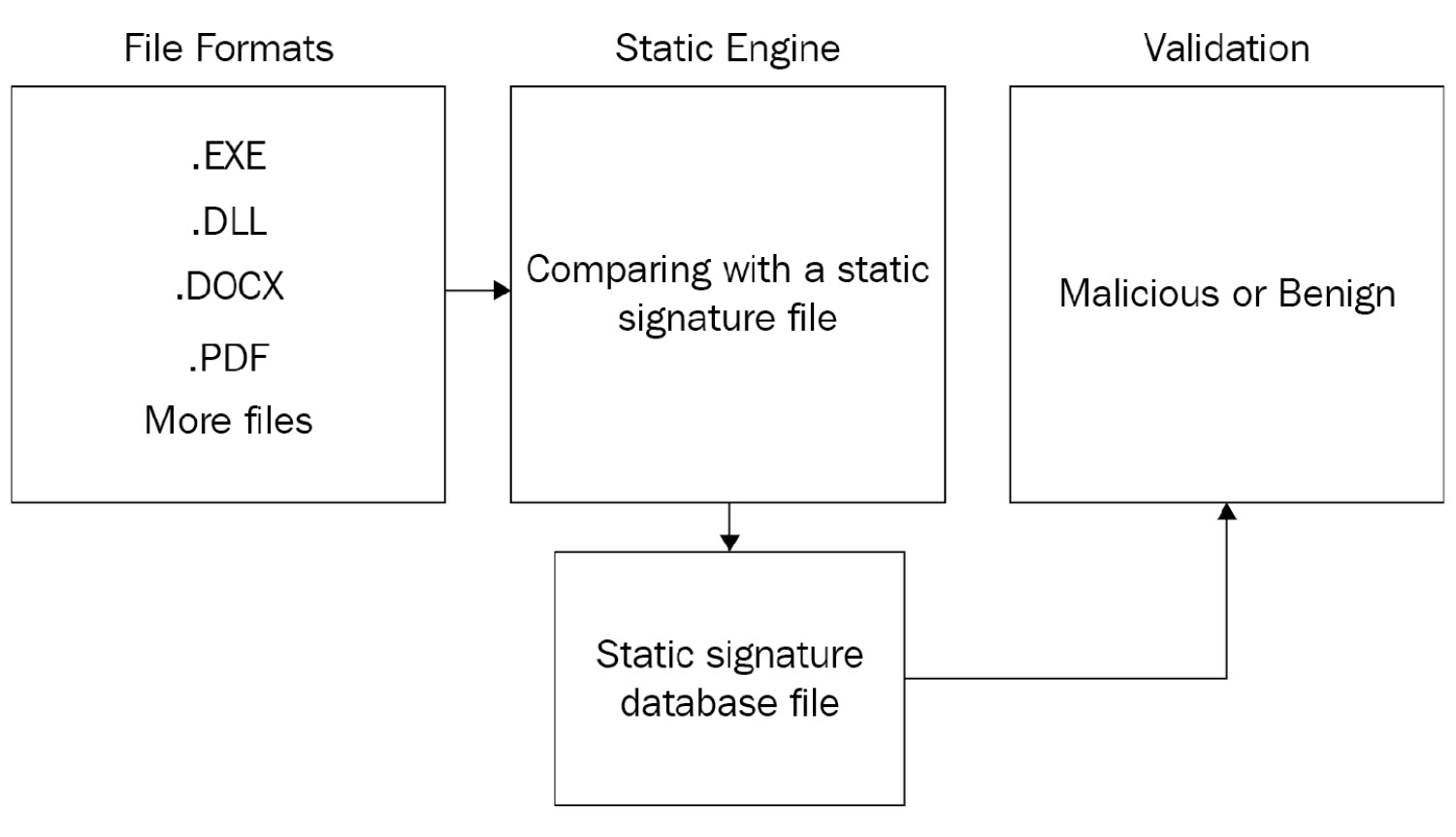
Collection of the Main Anti-Virus Detection and Bypass Techniques Such actions include disabling the Firewall, the Task Manager, the Command Prompt, the User Account Control, etc. This list is non-exhaustive and there exist multiple methods to bypass static analysis [ 4 ], such as the use of concealers [ 2 ]. However, the techniques remain the same: 1. Encrypt the program.
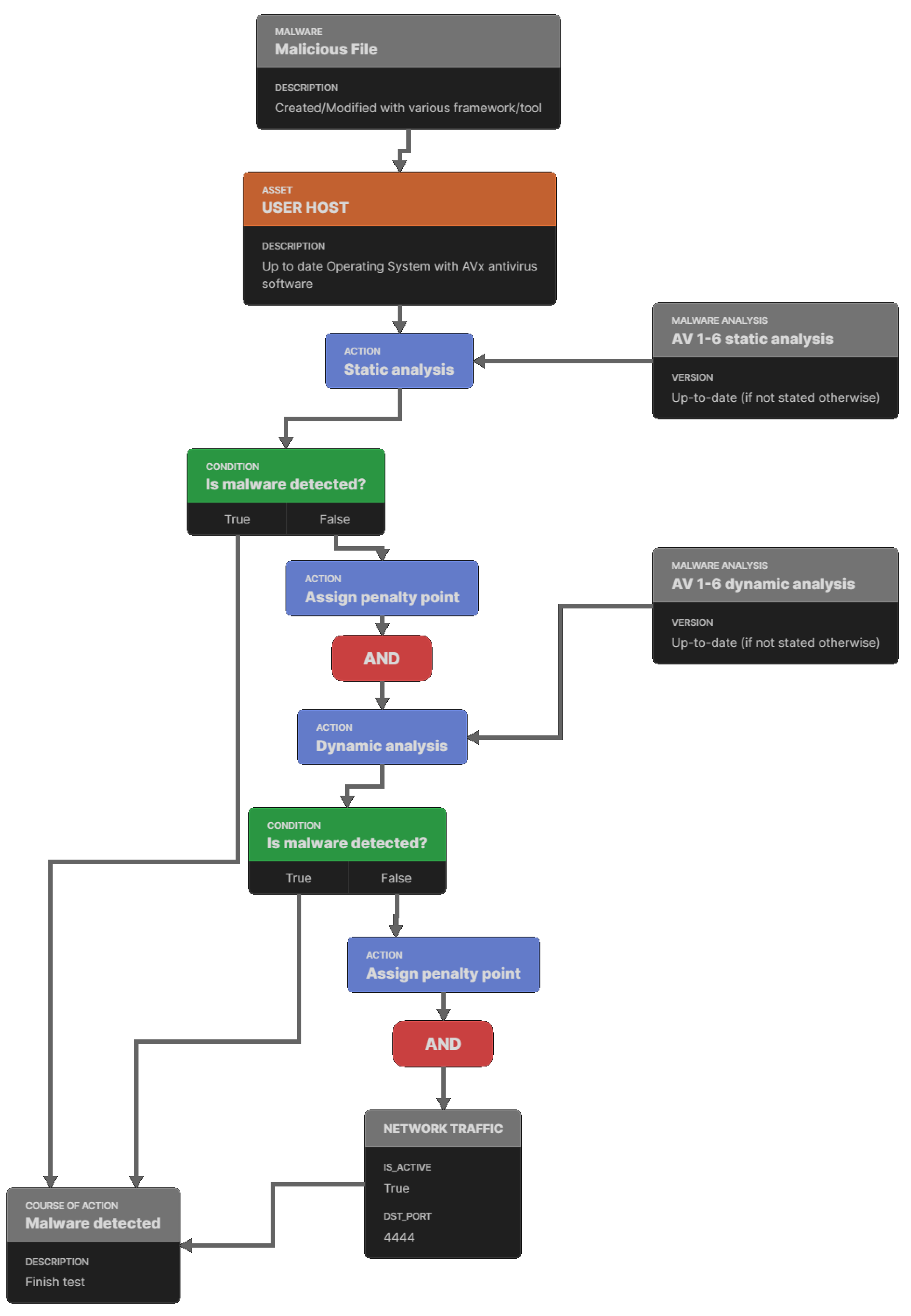
Common Antivirus Bypass Techniques | LMG Security Two well-known open-source examples of software utilizing many of the antivirus bypass techniques described above are: The Veil-Framework Shellter Sandboxing - Is the Malware "Sandbox Aware?" Sandboxing is another consideration for malware authors trying to avoid detection.
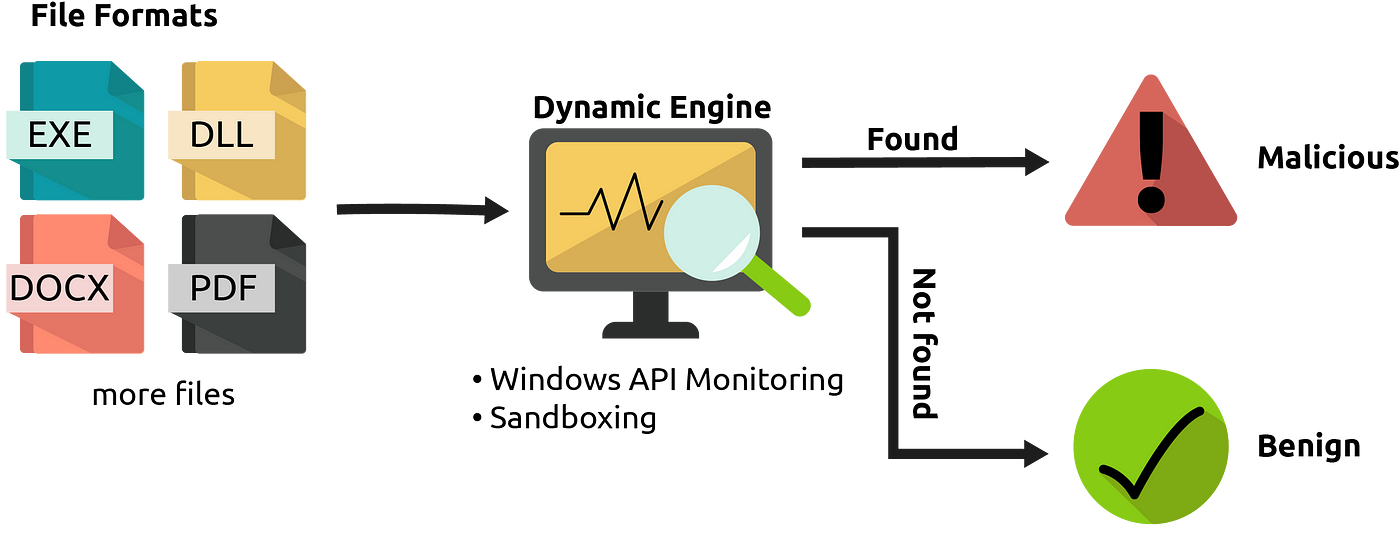
Art of Anti Detection 1 - Introduction to AV & Detection Techniques Heuristic analysis is a method employed by many computer antivirus programs designed to detect previously unknown computer viruses, as well as new variants of viruses already in the "wild".Heuristic analysis is an expert based analysis that determines the susceptibility of a system towards particular threat/risk using various decision rules or w...
(PDF-Doc) Antivirus Bypass Techniques Full Download | Finance PDF Antivirus Bypass Techniques PDF Download Are you looking for read ebook online? Search for your book and save it on your Kindle device, PC, phones or tablets. Download Antivirus Bypass Techniques PDF full book. Access full book title Antivirus Bypass Techniques by Nir Yehoshua. Download full books in PDF and EPUB format.
Fileless attacks: How attackers evade traditional AV and how to stop them Navigate to Configure > Policies. Click " New " or select an existing policy. Choose the " Endpoint Detection and Response " tab. Locate " Suspicious Activity Monitoring " and enable it for the desired operating systems. Suspicious Activity monitoring detections in Nebula showing a possible fileless attack.
Antivirus Evasion | Bypass Techniques. | by Dhanishtha Awasthi - Medium 5 min read Antivirus Evasion | Bypass Techniques. While playing around with machines I came up with a very interesting scenario, where my executable payloads on as soon as getting copied to...




![√DOWNLOAD [PDF]> Antivirus Bypass Techniques: Learn ...](https://pbs.twimg.com/profile_images/1422390936387035136/CwjBvCoj_400x400.jpg)





![PDF] Evolution of Computer Virus Concealment and Anti-Virus ...](https://d3i71xaburhd42.cloudfront.net/f66ec9eefb838197f51b292edbc921c7a7dc013c/3-Table1-1.png)










0 Response to "40 antivirus bypass techniques pdf"
Post a Comment